70以上 fortianalyzer log view filter syntax 112807-Fortianalyzer log view filter syntax
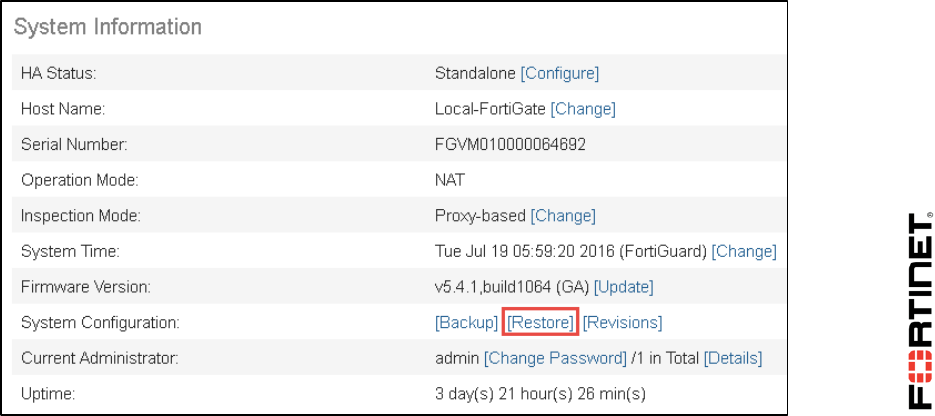
FortiAnalyzer Lack of visibility continues to extend breach and compromise events to an average of more than 100 days For each day an organization is exposed, it's another opportunity for attackers to get to sensitive customer and confidential information FortiAnalyzer is the NOCSOC security analysis tool built with operations perspectiveMultiple process may crash causing low insertion log rate and and missing Log View tab FortiAnalyzer is missing IO statistics in diagnostics report 5624 On FortiView's Top Sources, trying to filter logs for "Source !=xxxx" adds a filter for "User" causing incorrect data to be displayedLog View allows you to download a specific filtered view Log Browse allows you to download rolled logs FortiAnalyzer also provides the option to upload logs to a FTP, SFTP, or SCP server on a scheduled basis The CLI command execute backup logs sends everything for whatever device or devices you specify

Administration Guide Fortianalyzer 6 0 1 Fortinet Documentation Library
Fortianalyzer log view filter syntax
Fortianalyzer log view filter syntax-Deploy Fortinet FortiAnalyzer on Azure to collect, correlate, and analyze geographically and chronologically diverse security data Aggregate alerts and log information from Fortinet appliances and thirdparty devices in a single location, to get a simplified, consolidated view of Fortianalyzer We have a fortianalyzer and it is not seeing any logs when we go to Logs and Archive but according to the device statistics from the dashboard, it shows that the fortianalyzer is collecting logs just fine Testing connectivity from the Fortigate appliance works too to the analyzer It is just when we try to generate reports or




Cookbook Fortigate Fortios 6 2 0 Fortinet Documentation Library
Set the maximum number of admin users that be logged in at one time (1 256, default = 256) Enter the name of an https server certificate to use for secure connections (default = servercrt) FortiAnalyzer has servercrt and Fortinet_Local certificates preloaded Set the banner messages (character limit = 255)Has anyone had any luck with t7 rows To Filter FortiClient log messages Go to Log View > Traffic In the Add Filter box, type fct_devid=* A list of FortiGate traffic logs triggered by FortiClient is displayed In the message log list, select a FortiGate traffic log to view the details in the bottom pane Click the FortiClient tab, and doubleclick a FortiClient traffic log to
Comprehensive Log Analysis and Reporting For Fortigate Firewalls Firewall Analyzer fetches logs from Fortigate Firewall, analyzes policies, monitors security events and provides extensive Fortigate log reports (it also supports other firewalls)Firewall Analyzer supports logs received from Fortinet devices like FortiOS, and FortiGate The logging of Fortinet Referrer URLs needs to be configured per webfilter profile via the Fortinet command line To do this, use the following commands Text config webfilter profile edit Name of your profile set logallurl enable set webfilterrefererlog enable end Go to Log View, and select a log type In the content pane, customize the log view as needed by adding filters, specifying devices, and/or specifying a time period In the toolbar, click Custom View In the Name field, type a name for the new custom view Click OK The custom view is now displayed under Log View > Custom View To edit a custom
FortiAnalyzer platforms accept a full range of data from Fortinet solutions, including traffic, event, virus, attack, content filtering, and email filtering data It eliminates the need to manually search multiple log files or manually analyze multiple consoles when performing forensic analysis or network auditingThe metric filter syntax for JSON log events uses the following format {SELECTOR EQUALITY_OPERATOR STRING } The metric filter must be enclosed in curly braces {}, to indicate this is a JSON expression The metric filter contains the following parts SELECTOR Specifies what JSON property to check Property selectors always start with dollarThe FortiAnalyzer unit can display device logs in realtime, enabling you to view log messages as the FortiAnalyzer unit receives them Page 92 Viewing Historical Log Messages Viewing log messages Viewing historical log messages Figure 1 Viewing current logs Column Settings Devices Select the type of device you want to view logs from




Fortianalyzer 5 4 0 Beta 3 Release Notes Computer Architecture Computing




Victoria Martin Fortinet Cookbook
Create report 1 Create dataset To create a dataset goto the 'Reports' tab on your FortiAnalyzer then browse to Advanced > Dataset From here click on 'Create New' and enter a name, select Traffic for the 'Log Type' Once this is done you can click on the 'Test' button to make sure it's working correctly then click 'Ok' to saveQ4 21 videos 1 Introducing the FortiAnalyzer BigData 4500F;FortiAnalyzer's family of real time logging, analysis and reporting systems;



Fortinet Fortianalyzer Centralized Logging Analysis And Reporting



Http Pdfstream Manualsonline Com 8 8eb77a 5796 4a92 2b 49a6c3b4c0 Pdf
Came from pfSense From what I have read, it looks like 6010 is the way to go for stability A few hiccups along the way with DNS filter, SSL VPN DNSSuffix All resolved Watched the Fortinet Guru Picked up a few tips I have tested it with FortiClient 608 on Windows 10 I have read that it is the version for "Log on before Windows"FortiAnalyzer's web usage and browsing reports rely on hostname information being present in traffic logs To verify that it is, add the column 'Host Name' to display under Log View Reload the page and check if any traffic logs have an entry under 'Host Name'If you see a device, let's call it , making connections to a botnet in China, it is good odds that malware is doing the talking, not the user




Kibana Discover Punch Documentation




Fortianalyzer Administration Guide Version Pdf Free Download
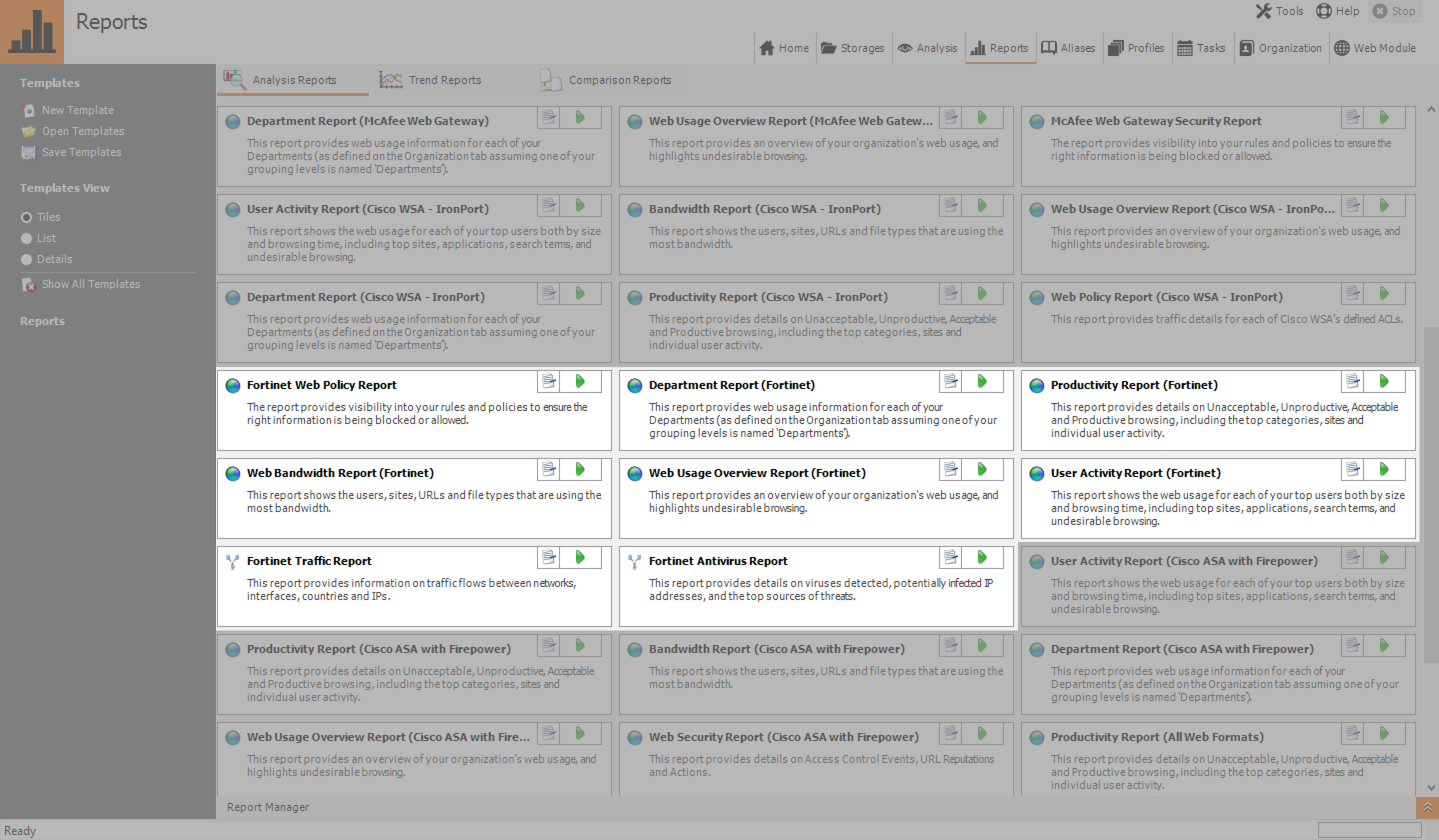
Dataset Reference List The following tables list the available predefined data sets reported by FortiAnalyzer For documentation and technical support reference purposes, thess tables contain the dataset names, SQL query syntax for each dataset, and the log category of the dataset Dataset Name Description Log Category TrafficBandwidthSummaryDayOfMonth TrafficDiagnose 1 Syntax diagnose sniffer packet Variable Description Type the name of a network interface whose packets you want to capture, such as port1 , or type any to capture packets on all network interfaces Type either none to capture all packets, or type aReal Time Network Protection Q4 21 videos 1 Introducing the FortiAnalyzer BigData 4500F;



Fortigate Report Dataset Sql Query




New Features Fortianalyzer 6 2 0 Fortinet Documentation Library
The correct syntax is cfgpath=firewall\policy To create an event handler using the Generic Text Filter to match raw log data Go to Log View, and select a log type In the toolbar, click Tools > Display Raw The easiest method is to copy the text string you want from the raw log and paste it into the Generic Text Filter fieldIt is a network hardware device designed specifically for these processes, which collects log data from Fortinet devices and third party devices safely" – Security Engineer ★★★★★ "Great Utility For Regulatory Compliance And Troubleshooting"Log, and report files on the FortiAnalyzer unit † Network sharing FortiAnalyzer units can use their hard disks as an NFS or Windowsstyle network share for FortiAnalyzer reports and logs, as well as users' files † FIPS support Federal Information Processing Standards (FIPS) are supported in some special releases of FortiAnalyzer firmware




Pdf Telecharger Fortianalyzer Rebuild Sql Database Gratuit Pdf Pdfprof Com



1
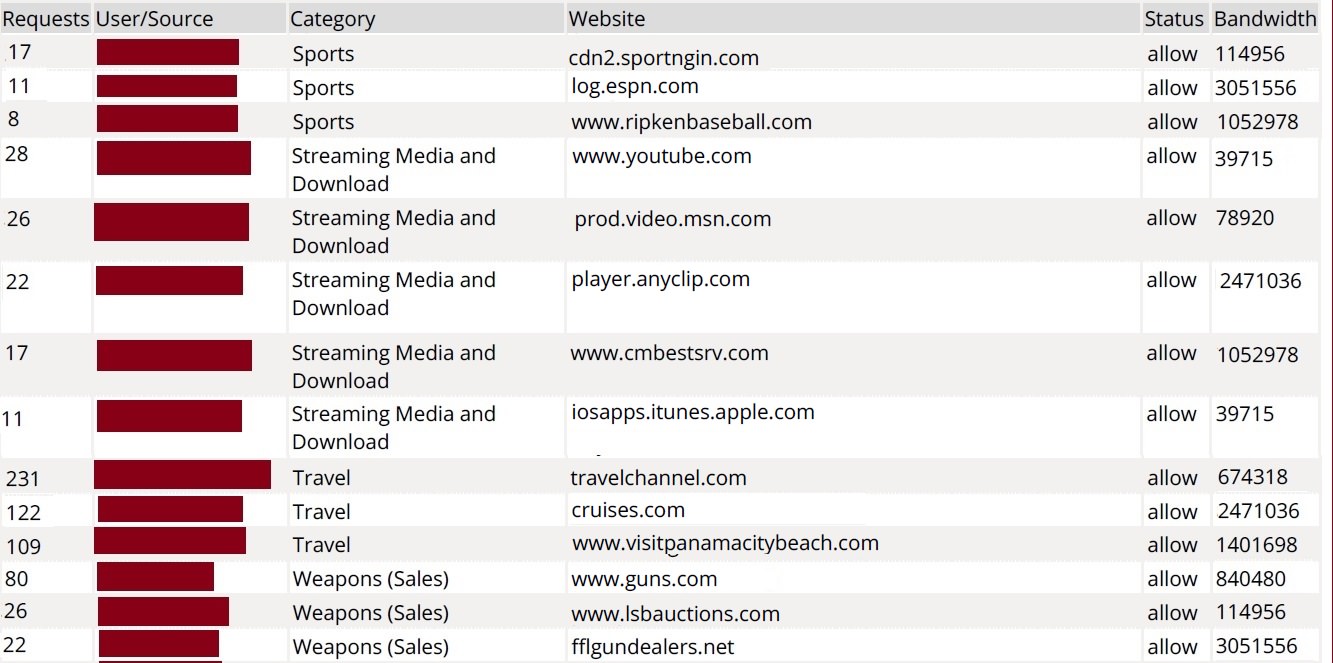
FortiAnalyzer can collect logs from managed FortiGate, FortiCarrier, FortiCache, FortiMail, FortiManager, FortiSandbox, FortiWeb, FortiClient, and syslog servers Following is a description of the types of logs FortiAnalyzer collects from each type of device Security Antivirus, Intrusion Prevention, Application Control, Web Filter, DNS, Data Hi guys, I' ve got a FA running 503 here and have been trying to figure out a way of applying a NOT filter to the log view For example, I' d like to look at the logs where scrip != but none of the filters seem to work (using NOT, !In FortiAnalyzer, under Reports > Datasets, there is a big variety of predefined queries, which cover most use cases for the data available in the different log types The Dataset names generally give some idea about what results to expect, but of course it is possible to review the SQL syntax for more details, and test the output




Troubleshooting Fortinet Document Library Manualzz




Fortianalyzer Administration Guide Version Pdf Free Download
FortiAnalyzer logs and analyzes aggregated log data from Fortinet devices and other syslogcompatible devices EventTracker examines this collective of logs and leverage machine learning to identify critical events, suspicious network traffic, configuration changes and user behaviour analytics EventTracker Enterprise gathers and examinesFortiGates support several log devices, such as FortiAnalyzer, FortiGate Cloud, and syslog servers Approximately 5% of memory is used for buffering logs sent to FortiAnalyzer The FortiGate system memory and local disk can also be configured to store logs, so it is also considered a log device Reports show the recorded activity in a more Advanced logs queries can be used in the Legacy Logs Viewer, the Logging API, or the gcloud commandline tool Note To write filters for sinks and logsbased metrics, you use the same syntax and expressions that are used to query your logs data For more basic querying options, go to Basic logs queries




Fortigate Cli Reference Fortinet Technical Documentation



Fortios Cli Reference For Fortios 5 0
2 Introducing the FortiGate 40FSynopsis Requirements Parameters Notes Examples Return Values Status Synopsis This module is able to configure a FortiGate or FortiOS by allowing the user to set and modify log_fortianalyzer feature and filter categoryIt looks like in the FortiView > Top Threats view that you can't combine operators I was playing around with it on our FAZ instance & am seeing similar results It looks like the proper search syntax in FortiView is threattype="Spam URLs" (catdesc seems to be limited to the Log View section) but even in looking at the help section for



Fortinetweb S3 Amazonaws Com Docs Fortinet Com V2 Attachments A070ad6d 1a08 11e9 9685 F8bc1258b856 Fortigate Fortios Log Message Reference Pdf




Passleader 100 Pass Ensure Fortinet Nse5 Dumps Vce And Dumps Pdf Question 26 Question 50 New Fortinet Exam Dumps From Passleader
FortiAnalyzer's Fabric View with Asset and Identity monitoring provides full SOC visibility of users and devices, including analytics of the attack surface and enables analysts to view and manage detailed UEBA information collected from logs and fabric devices, with filters2 Introducing the FortiGate 40F;FortiAnalyzer is Fortinet's Security Driven Analytics and Log Management Solution FortiAnalyzer offers organizations a way to centrally aggregate Fortinet logs in a central location, automate workflows and compliance reporting, and detect advanced threats If playback doesn't begin shortly, try restarting your device




Cookbook Fortigate Fortios 6 2 0 Fortinet Documentation Library




7 Key Configurations To Optimize Fortinet Fortigate S Logging And Reporting
Fortios_log_fortianalyzer_filter – Filters for FortiAnalyzer in Fortinet's FortiOS and FortiGate fortios_log_fortianalyzer_override_filter – Override filters for FortiAnalyzer in Fortinet's FortiOS and FortiGate fortios_log_fortianalyzer_override_setting – Override FortiAnalyzer settings in Fortinet's FortiOS and FortiGate FortiAnalyzer has no way of telling whether traffic logs are generated by a user or by a background process on the device For example;Contents FortiAnalyzer™ Version 40 MR2 Administration Guide Revision 13 3 http//docsfortinetcom/ • Feedback Contents Introduction




Fortianalyzer V5 0 Patch Release 6 Release Notes




Fortigate Cookbook Logging Traffic And Using Fortiview 5 4 Youtube
When local database is selected in FortiAnalyzer, the product uses postgres To generate custom reports you can use the funcions provided by postgres in SQL One used in several default reports is coalesce Other useful functions to_timestamp Useful for converting fileds like "itime" and "timestamp" of each log record Since their are stored in UNIXFilter Logs Each log has a filter area that allows you to set a criteria for which log entries to display The ability to filter logs is useful for focusing on events on your firewall that possess particular properties or attributes Filter logs by artifacts that are associated with individual log entries For example, filtering by the ruleIf you enable daylight saving time, the FortiAnalyzer unit automatically adjusts the system time when daylight saving time begins or ends defaultdiskquota This variable does not function on FortiAnalyzer defaultsearchmode {advanced filterbased} Set the default search mode of log view (default = filterbased)



Sg Netmarket Oss Ap Southeast 1 Aliyuncs Com 369cf41cb9bc853bcc12ccb3d Pdf




Al S Tech Corner How To Create A Ssl Vpn Login Report On A Fortianalyzer
Filter string syntax is parsed by FortiAnalyzer, escape characters must be use when needed, and both upper and lower case characters are supported For example "a ~ \"regexp\" and (c==d OR e==f)" logforward fortigate howto fortinet cli webgui FortiOS 5 troubleshooting fortianalyzer FortiOS 52 fortiauthenticator fortimanager logging fortimail 505 Q&A application control reporting 52 UTM config linux script ssl vpn two factor authentication web filter HA certification debug dlp forticache fortivoice ldap license policy radius route sms smtp sslClick Add Filter, select Application, type WidgetPro If you do not find the application in the filtered results, go to Log View > Traffic Click the Add Filter box, select Source IP, type the source IP address, and click Go Analyzing and reporting on network traffic A new administrator starts at #1 Technical College




Cookbook Fortigate Fortios 6 2 4 Fortinet Documentation Library




Cookbook Fortigate Fortios 6 2 0 Fortinet Documentation Library
Just go to Log View and use the Add filter at the top to find what you're looking for out to excel if you need 0 Pimiento OP spiceheadaihwt at 0333 UTC I am trying to do that using fortianalyzer APIs through code ie obtaining the sha1/base64 of the contents of only those files whose fsaverdict is not clean (IA FortiGate is bestofbreed and is in Gartner's top right quadrant for NGFWs B FortiManager and FortiAnalyzer provide prebuilt regulatory reports, capable of identifying deficiencies in your network C FortiManager and FortiAnalyzer can identify and3 Leverage SAML to switch between two FortiGates



Fortinetweb S3 Amazonaws Com Docs Fortinet Com V2 Attachments 7f9ac9 Dbb3 11e8 B86b a Fortianalyzer 6 2 0 Administration Guide Pdf




Setup Remote Logging To Fortianalyzer For Forticlient Youtube
Etc) seems to work!



Create A Fortianalyzer Custom Report To See Which Users Are Spending The Most Time Browsing And Goofing Off




Fortimanager V5 0 10 Release Notes



How To Configure Fortinet Fortigate Logging And Reporting




Cookbook Fortigate Fortios 6 2 0 Fortinet Documentation Library




Fortigate Multi Threat Security System Helge Net




Fortianalyzer Fortinet Guru



How To Configure Fortinet Fortigate Logging And Reporting



Fortinetweb S3 Amazonaws Com Docs Fortinet Com V2 Attachments 7f9ac9 Dbb3 11e8 B86b a Fortianalyzer 6 2 0 Administration Guide Pdf



1




Fortianalyzer Administration Guide Manualzz




Fortianalyzer Administration Guide Version Pdf Free Download




Pdf Telecharger Fortianalyzer Log Retention Gratuit Pdf Pdfprof Com




Ken Felix Security Blog Using Execute Log Filters To Monitor Firewall Traffic




Administration Guide Fortigate Fortios 6 4 4 Fortinet Documentation Library




Fortigate Logging Reporting Backup Command Line Interface




New Features Fortianalyzer 6 2 1 Fortinet Documentation Library



Fortigate I Student Guide Forti Gate Online V2



How Clear Logs Fortigate Fasrgetmy



Fortinetweb S3 Amazonaws Com Docs Fortinet Com V2 Attachments 492e0e84 136b 11e9 B86b a Fortianalyzer 6 0 4 Administration Guide Pdf




Fortianalyzer Administration Guide Version Pdf Free Download



Documentation Nokia Com Cgi Bin Dbaccessfilename Cgi V1 Fortigate ips user guide Pdf




Tutorial 5 4 07 Fortimanager Diagnostics And Troubleshooting Fortinet Network Security Specialist Nse5 Programmer Sought




Fortianalyzer And Fortigate Sql Log Database Query Technical Manualzz



Fortimanager Cli Reference Fortinet Document Library Manualzz



Www Netsurion Com Corporate Media Corporate Files Support Docs Integration Guide Fortigate Firewall Pdf




Fortianalyzer 5 0 Cli Reference Manualzz



Http Docshare02 Docshare Tips Files 4210 Pdf




7 Key Configurations To Optimize Fortinet Fortigate S Logging And Reporting



Fortinetweb S3 Amazonaws Com Docs Fortinet Com V2 Attachments 32cb817d A307 11eb 0b a Fortianalyzer 7 0 0 Administration Guide Pdf




New Features Fortigate Fortios 6 2 0 Fortinet Documentation Library




Pdf Telecharger Fortianalyzer Log Retention Gratuit Pdf Pdfprof Com




Pdf Telecharger Fortianalyzer Log Retention Gratuit Pdf Pdfprof Com




New Features Fortianalyzer 6 2 0 Fortinet Documentation Library




Victoria Martin Fortinet Cookbook
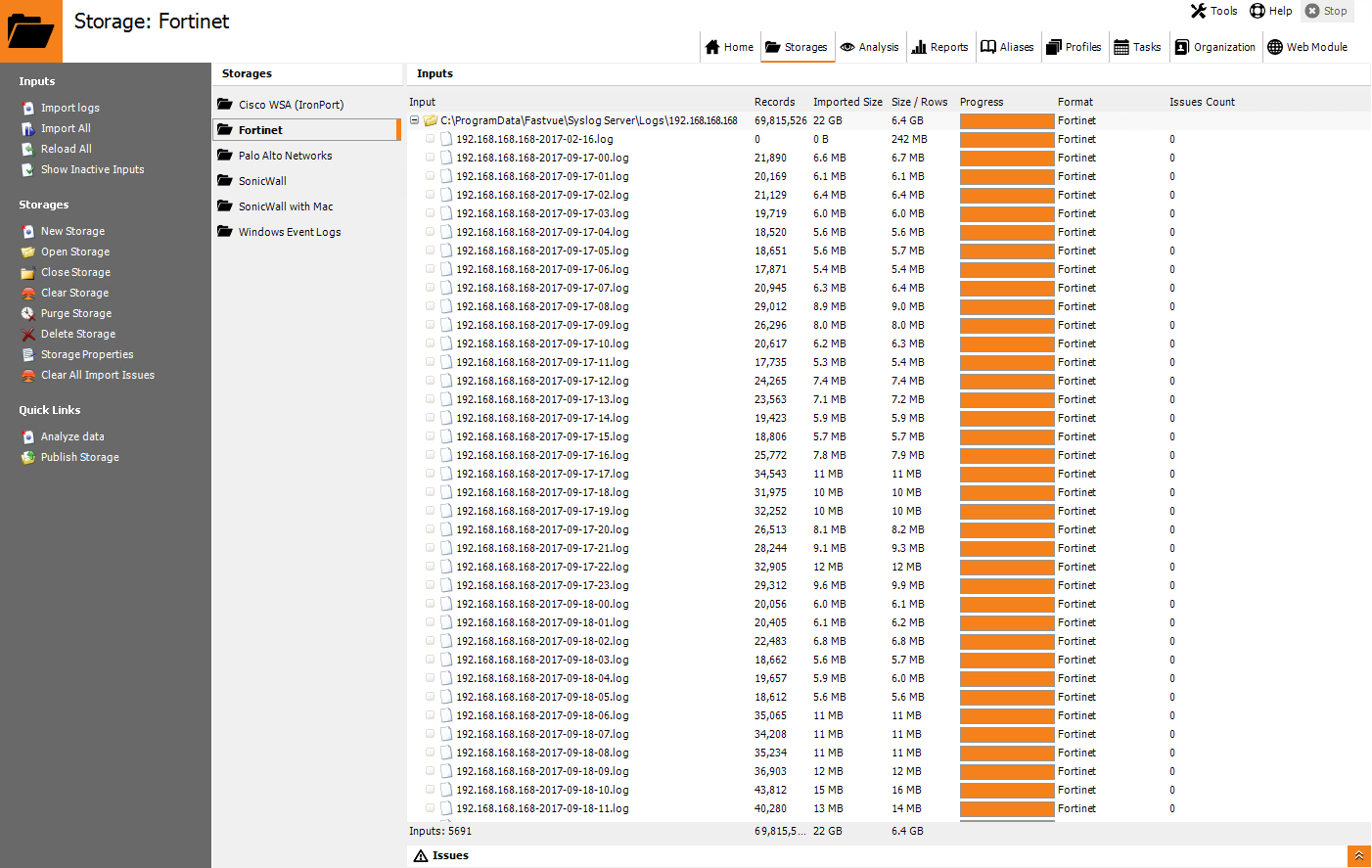



How To Configure Fortinet Fortigate Logging And Reporting



Fortinetweb S3 Amazonaws Com Docs Fortinet Com V2 Attachments 7f9ac9 Dbb3 11e8 B86b a Fortianalyzer 6 2 0 Administration Guide Pdf



Fortimanager V5 0 10 Release Notes




Fortianalyzer 6 0 Study Guide Online Superuser Radius



1



Fortinetweb S3 Amazonaws Com Docs Fortinet Com V2 Attachments 7f9ac9 Dbb3 11e8 B86b a Fortianalyzer 6 2 0 Administration Guide Pdf



Fortinetweb S3 Amazonaws Com Docs Fortinet Com V2 Attachments 492e0e84 136b 11e9 B86b a Fortianalyzer 6 0 4 Administration Guide Pdf




New Features Fortianalyzer 6 2 0 Fortinet Documentation Library




Fortianalyzer Admin 40 Mr3 Command Line Interface Databases




Fortianalyzer 6 0 0 Administration Guide Concursos 8




Custom Fortianalyzer Report To See Blocked Urls For A Category Fortinet Guru




Fortianalyzer Fortinet Guru




7 Key Configurations To Optimize Fortinet Fortigate S Logging And Reporting




Fortianalyzer 6 2 Study Guide Online
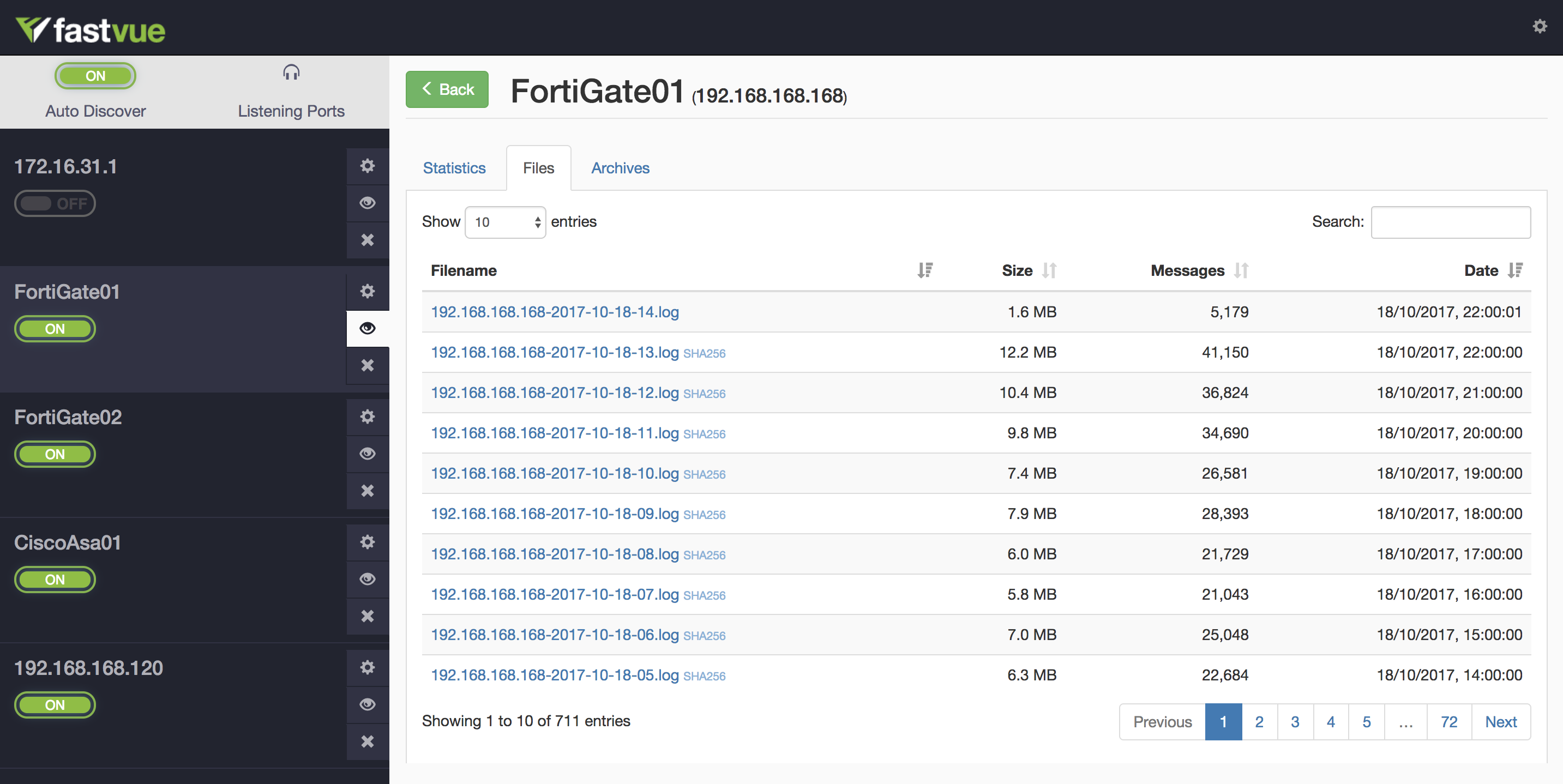



How To Configure Fortinet Fortigate Logging And Reporting




Fortianalyzer Report Overview Youtube



Www Netsurion Com Corporate Media Corporate Files Support Docs Integration Guide Fortigate Firewall Pdf




Fortimanager Administration Guide




Administration Guide Fortianalyzer 6 0 1 Fortinet Documentation Library




New Features Fortigate Fortios 6 2 0 Fortinet Documentation Library




Pdf Telecharger Fortianalyzer Rebuild Sql Database Gratuit Pdf Pdfprof Com



Www Sans Org Reading Room Whitepapers Standards Architecting Compliance Case Study Mapping Controls Security Frameworks




Fortimanager Administration Guide




Fortianalyzer Administration Guide Version Pdf Free Download



Fortinetweb S3 Amazonaws Com Docs Fortinet Com V2 Attachments 6c4fe9fe 7369 11ea 9384 a Fortianalyzer 6 4 0 Administration Guide Pdf




Tutorial 5 4 07 Fortimanager Diagnostics And Troubleshooting Fortinet Network Security Specialist Nse5 Programmer Sought




Pdf Telecharger Fortianalyzer Rebuild Sql Database Gratuit Pdf Pdfprof Com




Fortianalyzer Administration Guide Version Pdf Free Download



Fortinetweb S3 Amazonaws Com Docs Fortinet Com V2 Attachments 32cb817d A307 11eb 0b a Fortianalyzer 7 0 0 Administration Guide Pdf



Http Pdfstream Manualsonline Com 8 8eb77a 5796 4a92 2b 49a6c3b4c0 Pdf




Fortianalyzer 5 4 5 Administration Guide Databases Computer Data Storage



Http Pdfstream Manualsonline Com 8 8eb77a 5796 4a92 2b 49a6c3b4c0 Pdf




Pdf Telecharger Fortianalyzer Log Retention Gratuit Pdf Pdfprof Com




Cookbook Fortigate Fortios 6 2 0 Fortinet Documentation Library




Administration Guide Fortimanager 6 2 0 Fortinet Documentation Library




Cookbook Fortigate Fortios 6 2 0 Fortinet Documentation Library




Cookbook Fortigate Fortios 6 2 3 Fortinet Documentation Library




Pdf Fortianalyzer Administration Guide Felipe Abastante Academia Edu




Ken Felix Security Blog Using Execute Log Filters To Monitor Firewall Traffic




Al S Tech Corner How To Create A Ssl Vpn Login Report On A Fortianalyzer
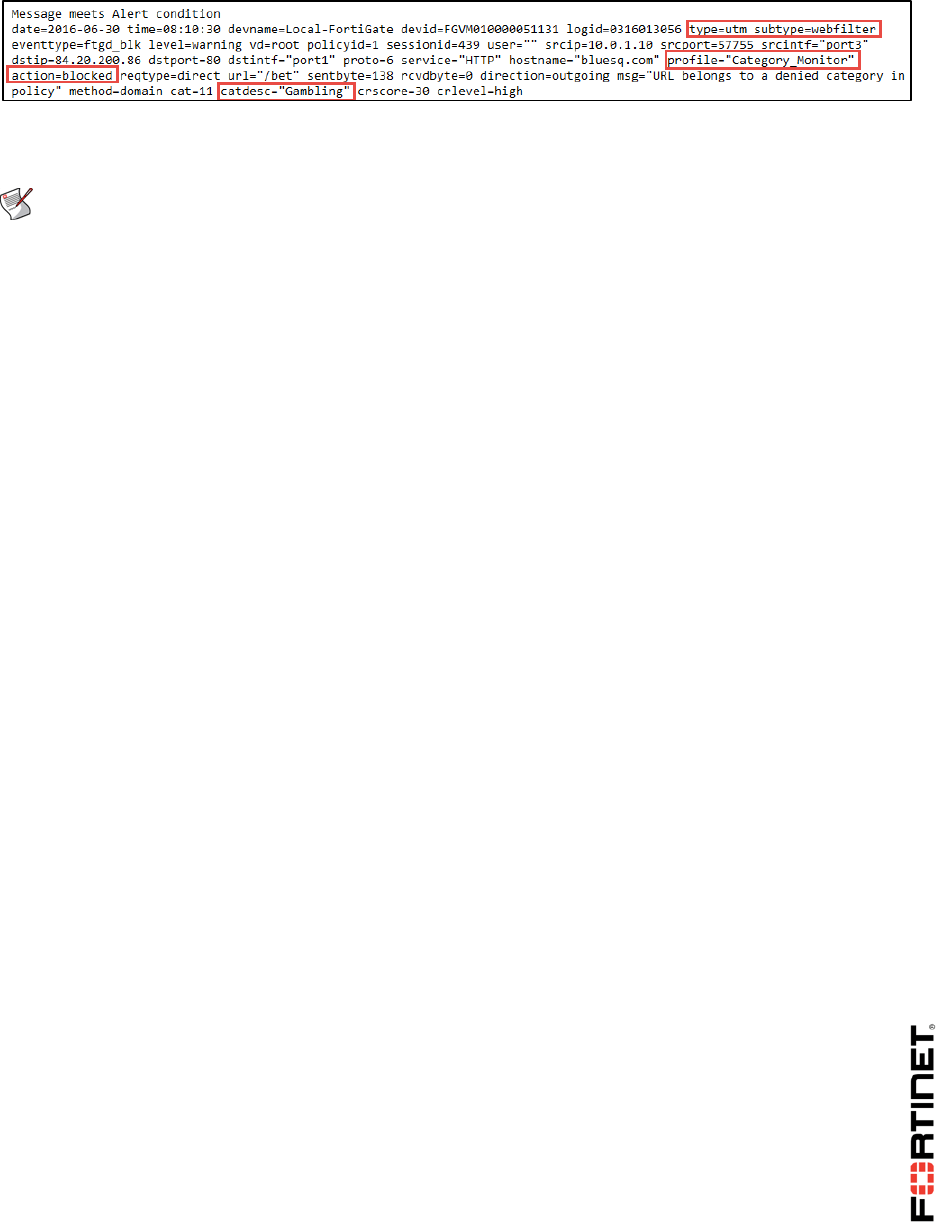



Fortigate I Student Guide Forti Gate Online V2




Logging And Reporting Fortinet Technical Documentation




New Features Fortigate Fortios 6 2 0 Fortinet Documentation Library


コメント
コメントを投稿